What is a Linux namespace and how does it facilitate container isolation?
Namespace isolation establishes logical boundaries for each container’s processes, networks, and resources to enable the safe and efficient execution of multiple containers on the same system.
It’s like being at a busy party, but instead of being in the same room, each individual is placed in a separate, soundproofed room. Each room has the same layout, but the person inside cannot see or hear anyone else. No one knows who’s in the other rooms, and each room has its own "local" environment, such as music, conversations, or even temperature. While the rooms all share a common building, each one feels like its own independent unit.
This is how container isolation works. Each container has its own isolated environment, allowing processes to function independently within their own namespace as if they were the only ones running on the system. Despite sharing the same underlying hardware, containers behave as if they’re running on separate machines. Each container runs in its own namespace and cannot access or interact with the resources of other containers unless specifically allowed. This isolation keeps containers lightweight and secure.
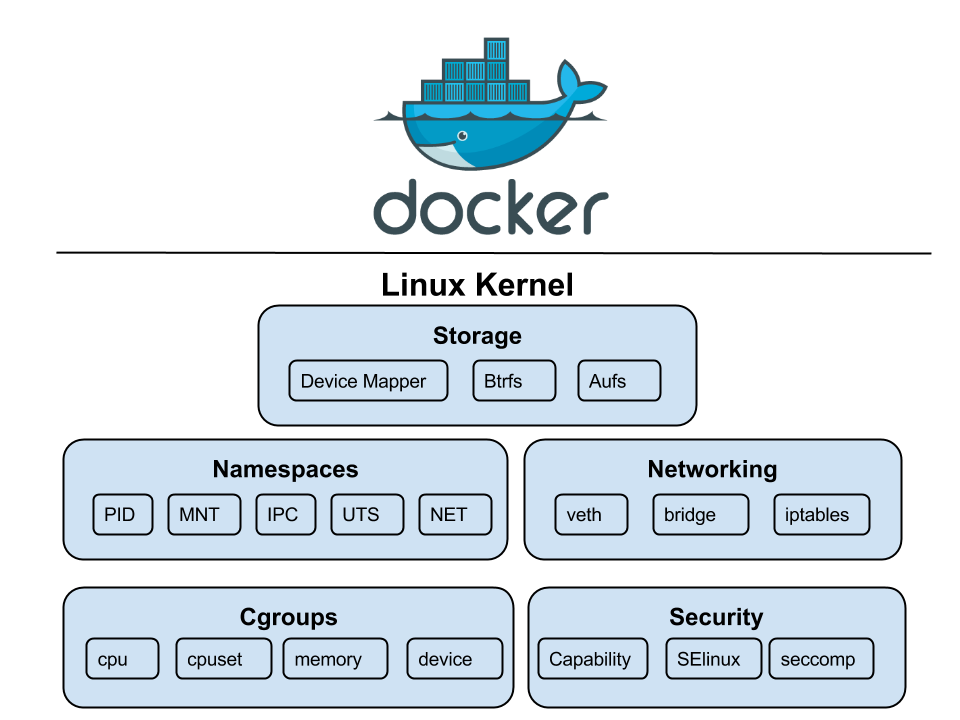
Types of namespaces in containers
There are several types of namespaces in Linux, each responsible for isolating a specific aspect of the system. Let’s break them down:
PID (Process IDs)
The PID namespace provides an isolated view of process IDs. A container only sees the processes that run within itself. For example, Container A may have a process with PID 1 (the first process), but Container B can also have a process with PID 1, even though they both run on the same physical host.
Without PID namespaces, containers would have conflicts when sharing process IDs, leading to issues with controlling and managing processes.
NET (Networking)
The NET namespace isolates each container’s network interfaces, IP addresses, routing tables, and ports. Each container has a virtual network, and the networking stack appears entirely separate from the host system and other containers. This prevents containers from interfering with each other’s network traffic. Each container can have its own IP address, and virtual networks and firewalls can securely control traffic between containers.
MNT (Mounts)
The MNT namespace isolates the file system mount points so containers have a separate view of the file system. A container may be mounted to a specific directory in the host file system (for example, /data), but other containers won’t have access to the same file system unless explicitly granted.
This ensures that containers cannot interfere with each other’s data and protects the host file system from accidental or malicious changes.
UTS (Host and Domain Names)
The UTS namespace isolates the hostname and domain name. Each container can have a hostname that is independent of the host system or other containers. This allows applications running in containers to operate as though they are on individual machines. It also ensures that containers don't inadvertently change the hostname of the host system or other containers.
IPC (Inter-process Communication)
The IPC namespace isolates IPC resources such as semaphores, message queues, and shared memory. Containers are restricted from accessing or interfering with IPC resources used by other containers.
USER (User and Group IDs)
The USER namespace provides isolation for user and group IDs so processes inside containers can run with different user privileges than those on the host system. For example, a container can run a process as root (UID 0) within its own namespace, but the user might be mapped to a non-root user on the host.
This enhances security since, even if a process inside a container runs with root privileges, it cannot access host system resources as root. This reduces the risk of privilege escalation attacks.
Benefits of container isolation in a Linux Namespace
Containers are lightweight compared to traditional virtual machines since they don’t require full operating system instances. They are ideal for multi-tenant applications since each container is customizable with its own hostname, network configuration, etc. This also allows independent container management, monitoring, and observability. Tools like Docker make it easier to automate the creation, deployment, and orchestration of containers.
Importantly, even if one container is compromised, isolation minimizes the risk of an attack spreading to other containers.
Example of namespace isolation in action
Let’s create two Docker containers (container1 and container2) to walk through a simple example using Docker:
docker run -d --name container1 ubuntu sleep 1000docker run -d --name container2 ubuntu sleep 1000
By default, Docker uses the following namespaces:
- PID Namespace:
container1andcontainer2have separate PIDs. - NET Namespace: Each container will have its own network interface, separate IP addresses, and routing tables. For instance,
container1might have IP172.17.0.2, andcontainer2will have172.17.0.3. Even though they’re on the same physical host, their networks are isolated. - MNT Namespace: Each container has its own file system and mounts. The directories inside
container1andcontainer2are completely isolated.
To view the isolation firsthand, you can see that there are two different PIDs for each container despite running the same process (sleep 1000):
docker inspect --format '{{.State.Pid}}' container1docker inspect --format '{{.State.Pid}}' container2
To check the IP addresses of the different containers, run the following commands:
docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' container1docker inspect -f '{{range .NetworkSettings.Networks}}{{.IPAddress}}{{end}}' container2
