SSL/TLS and Handshaking
What are SSL and TLS?
The Secure Sockets Layer (SSL) and Transport Layer Security (TLS) are protocols that encrypt information transmitted through the Hypertext Transfer Protocol (HTTP). When your connection to a web server is secured using SSL or TLS, the URL in your browser uses the acronym HTTPS instead of HTTP. Some browser bars post a padlock symbol. This indicates that the transmitted information is encrypted, and can't be read by malicious actors even if they intercept it.
What's the difference between TLS and SSL?
SSL, developed by Netscape, is the earlier version of TLS. Both of these protocols encrypt information transmitted through HTTP, but TLS is updated and has some improvements. However, these terms are often used interchangeably.
How TLS secures connections
Before a website or web application can use TLS, an SSL/TLS certificate must be installed on the web server. The certificate contains information about domain ownership, along with the server's public key. Both are essential for validating the server's identity.
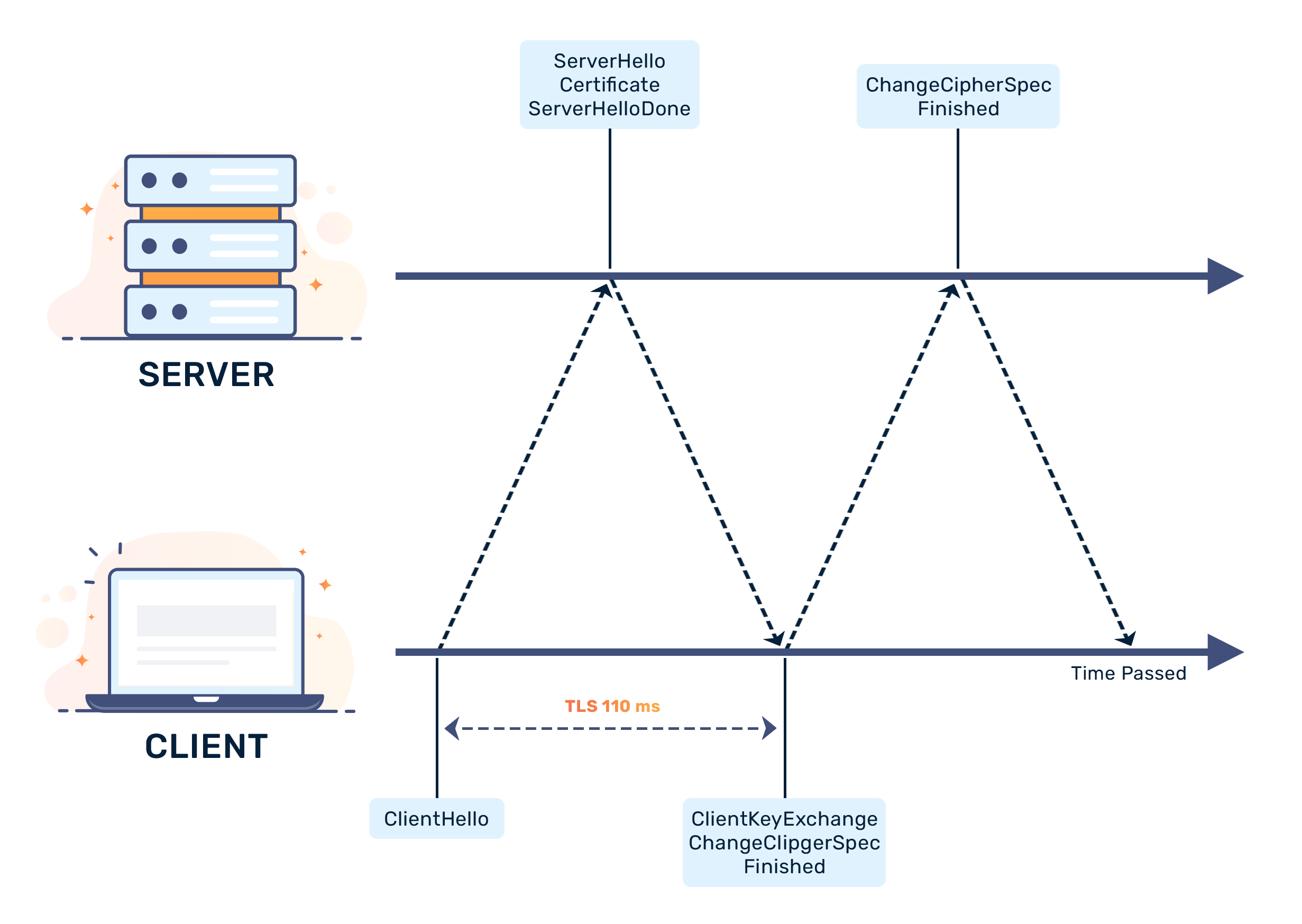
In order to start secure information transmission between the web server and the client (e.g. a web browser) using TLS, both must engage in a “handshake” to introduce themselves and establish a relationship. The TLS handshake establishes the following:
- The TLS version
- The encryption algorithms used in the handshake
- The authenticity of the TLS/SSL certificate
- Session keys to encrypt information transmission following the handshake
More about the TLS handshake process
The TLS handshake uses a process called asymmetric encryption. Asymmetric encryption uses public-private key pairs instead of a single key. Public keys can be distributed publicly, but the private key is held exclusively by the web server. Any client with a public key can decrypt a message encrypted with the server's private key to verify the message came from the server. The client verifies a certificate with an issuing authority, and then gets the public key from the TLS/SSL certificate.
During TLS, both sides must establish a master key to encrypt and decrypt all future data exchanges. To establish the master key, the client sends a pre-master key (encrypted using the public key obtained from the SSL certificate) to the server. The server is the only one who can decrypt this key, because nobody else holds the corresponding private key (asymmetric cryptography). Once the client confirms the server's identity, both sides can compute a secret shared session key from the pre-master key.
The client sends a message to the server encrypted using the secret shared session key. If the server successfully decrypts the message, it sends a message to the client encrypted with the secret shared session key. If the client also successfully decrypts the message, the TLS handshake process completes. Both sides will encrypt all future communication after the handshake using the same secret shared session key. This is known as symmetric encryption.
If you're still curious, you can read the official TLS specifications here.
