What are Reverse Proxies?
Introduction
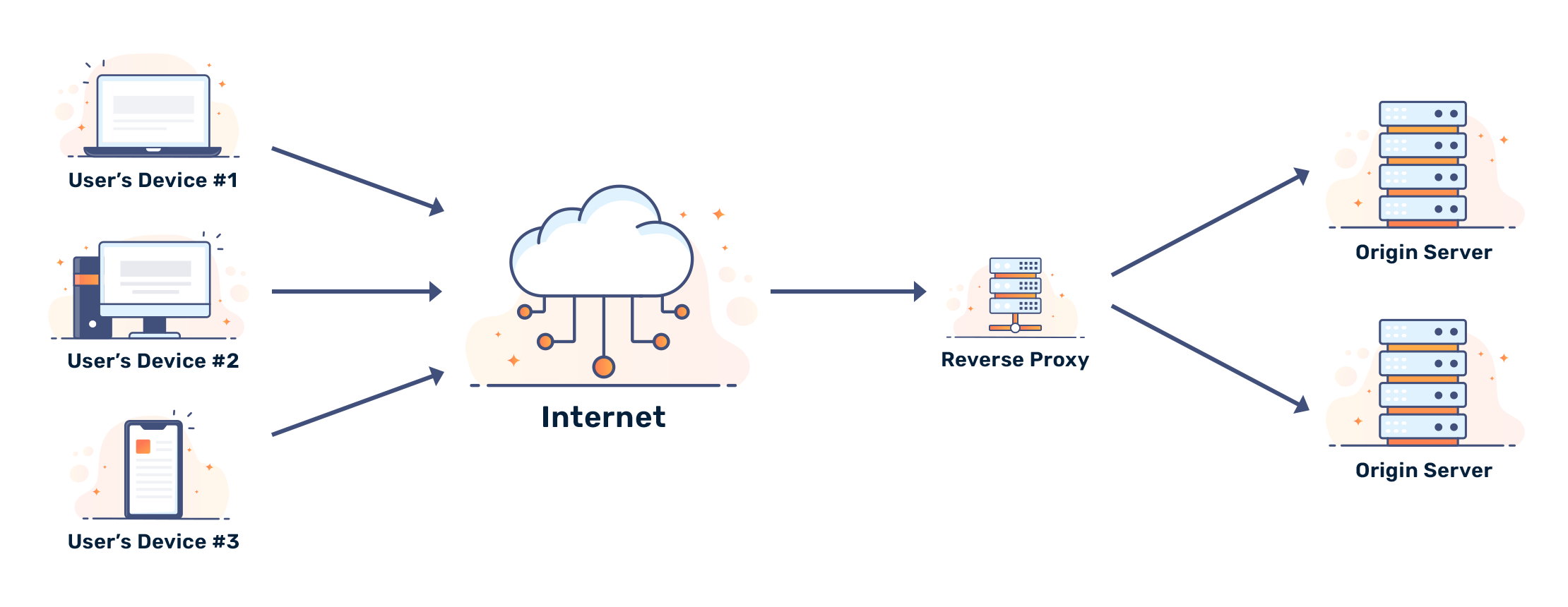
Reverse proxies are server-side proxies, as opposed to regular HTTP proxies, which are client-side. Reverse proxies hide the true identity of the origin server. They receive an HTTP/HTTPS request and forward information between the client and the origin. By acting as a middleman, reverse proxies prevent users from accessing content directly.
As a result, reverse proxies are found in DDoS protection applications, where end users can't discover the website's direct IP. Hiding the direct IP prevents malicious actors from taking a website or application offline.
How reverse proxies work
A reverse proxy passes along a user's header information so the origin knows what to serve. To start, a reverse proxy usually forwards the Host header. Popular software, such as NGINX, supports the ability to forward web sockets and newer HTTP connection types like partial QUIC support.
Other Uses For Reverse Proxies
Reverse proxies are commonly used to hide the identity of an origin server, but they can also be used to balance traffic across multiple origins.
For example, a CDN uses a PULL zone. The CDN pulls data through a node, caches static data, and forwards the data to users. Users see faster load times. Even if you request content from a server located thousands of kilometers away, you should see a smaller performance hit than you would if you requested content directly.
Popular reverse proxy software
Generally, you will hear about NGINX, Apache, and other web servers being mentioned. These servers have two modes of operation:
- Serving content from a local directory
- Acting as a reverse proxy
There are dedicated reverse proxies as well, such as HAProxy and Varnish.
CDNs vs. reverse proxies
Most CDNs have a PULL zone type. This uses a user-operated backend and many nodes placed in front.
This example uses a single reverse proxy:
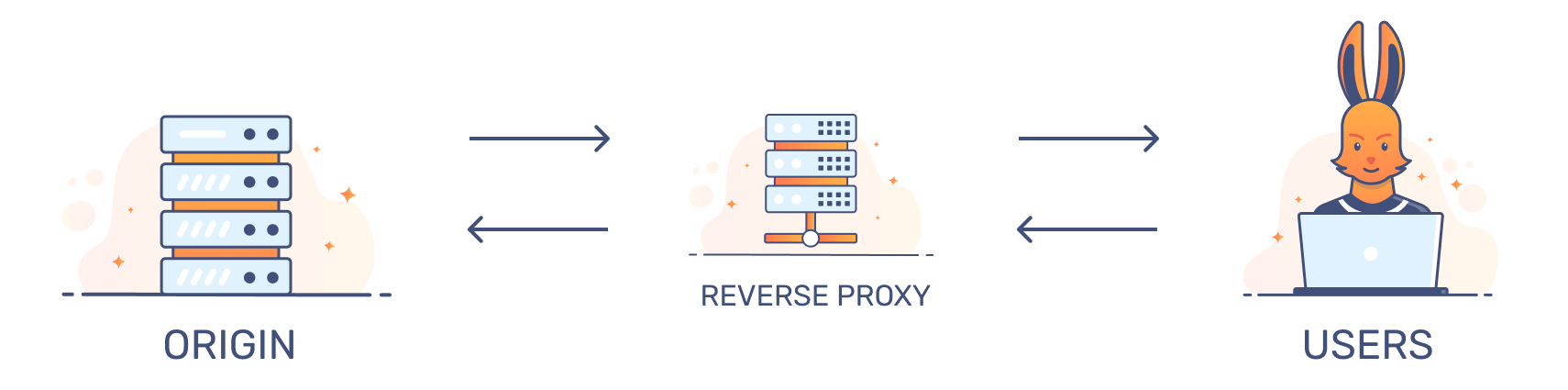
While pull zones and reverse proxies are similar, CDNs have other features that not all reverse proxies support.
