What is IPv4?
Unlike the speed of communication on the internet, we all know physical mail is slow. However, one thing remains the same: you need an address to send information. A person mails a note, message, or, hopefully, some cool Bunny merch to a recipient. The recipient then sees the address of the sender and can choose whether to open the letter or package or even respond to the sender’s address with a message of their own.
The difference lies in what the address looks like. Instead of numbers and words like a home address uses, internet addresses use numbers defined by the Internet Protocol (IP). That, and the fact that what you send is chopped up and sent in multiple packages, often called packets, through a process called fragmentation. It’s a lot like someone mailed your Bunny merch one sleeve at a time, and you have to sew it back together.
A final piece to our analogy is the network routers, which are like mail sorters at different post offices worldwide to ensure packages (packets) are routed ever closer to their destination.
IP version 4 (IPv4) was the first major Internet Protocol version defined in RFC 791 in 1981 and first deployed in 1982. It is still the dominant Internet Protocol. Let’s take a closer look at how IPv4 addressing works.
What is IPv4 addressing
IPv4 addresses are generally presented in dot-decimal notation, which consists of four octets (four groups of eight bits) of numbers separated by periods; for example, 198.51.100.1.
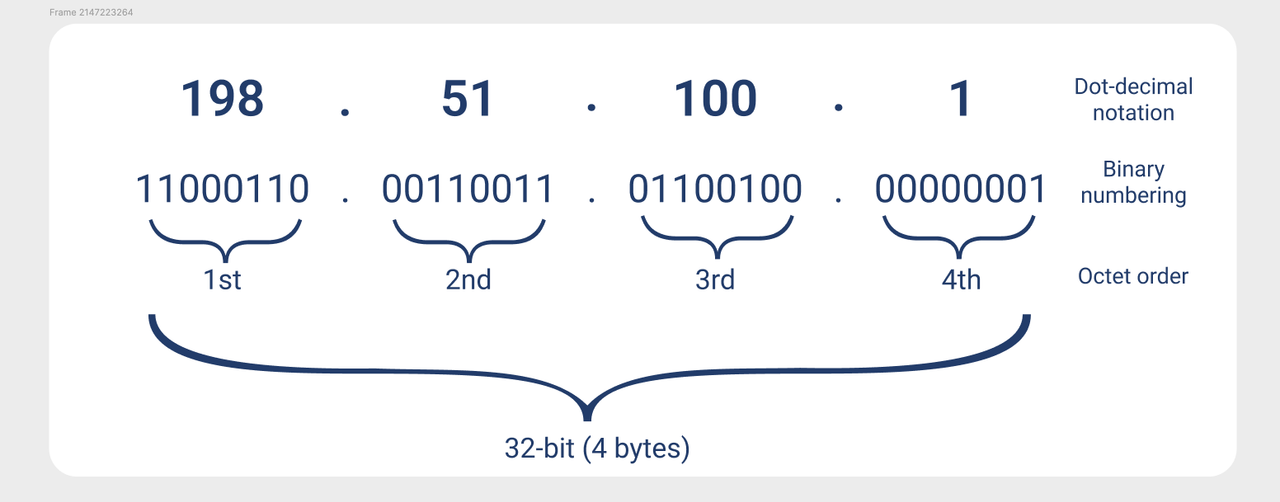 Figure 1: Dot-decimal versus binary IPv4 address notation.
Figure 1: Dot-decimal versus binary IPv4 address notation.
Each address is split into two parts: the network and the host. The network tells the internet which hosts are related. This distinction speeds up routing decisions since routers can just check which network the traffic belongs to instead of knowing the location of billions of individual IPs. It’s like getting off an elevator at a hotel and seeing a sign that shows rooms 200 to 214 are down the hallway to your left, and rooms 215 to 230 are to the right. A router just needs to know where the related groups of networks are.
For example, in the address 198.51.100.1, 198.51.100 is the network identifier, and the last octet .1 is the host identifier. In this case, the network identifier takes the first 24 bits and makes them static, and the host identifier takes the remaining 8 bits, where each possible value represents a single host. The network identifier can also be represented in slash notation: 198.51.100.1/24.
We usually reference the hosts on the internet through domain names or URLs rather than IP addresses. Domain names are translated to IP addresses and vice versa during DNS resolution, which is performed by the Domain Name System (DNS).
First and last IPv4 subnet addresses
The subnetwork and the broadcast address should not be used by any host. The first address in a subnetwork is reserved and used to identify the subnet. This is the address where all host bits are 0. The last address in a subnet is also reserved and used as a broadcast address. This is the address where all host bits are 1. For the example network 198.51.100.0/24, we have the following subnetwork and broadcast addresses:
| Type | Binary form | Dot-decimal notation |
|---|---|---|
| Subnetwork address | 11000110.00110011.01100100.00000000 | 198.51.100.0/24 |
| Broadcast address | 11000110.00110011.01100100.11111111 | 198.51.100.255/24 |
Reserved IPv4 addresses
The Internet Engineering Task Force (IETF) and the Internet Assigned Numbers Authority (IANA) restrict the use of various reserved IP addresses for special purposes. These IPs cannot be used for public IP addresses:
| Address block | Address range | Number of addresses | Scope | Description |
|---|---|---|---|---|
| 0.0.0.0/8 | 0.0.0.0–0.255.255.255 | 16,777,216 | Software | Current network. |
| 10.0.0.0/8 | 10.0.0.0–10.255.255.255 | 16,777,216 | Private network | Used for local communications within a private network. |
| 100.64.0.0/10 | 100.64.0.0–100.127.255.255 | 4,194,304 | Reserved network | Shared address space for communications between a service provider and its subscribers when using a carrier-grade NAT. |
| 127.0.0.0/8 | 127.0.0.0–127.255.255.255 | 16,777,216 | Host | Used for loopback addresses to the local host. |
| 169.254.0.0/16 | 169.254.0.0–169.254.255.255 | 65,536 | Subnet | Used for link-local addresses between two hosts on a single link when no IP address is otherwise specified, such as would have normally been retrieved from a DHCP server. |
| 172.16.0.0/12 | 172.16.0.0–172.31.255.255 | 1,048,576 | Private network | Used for local communications within a private network. |
| 192.0.0.0/24 | 192.0.0.0–192.0.0.255 | 256 | Reserved network | IETF Protocol Assignments, DS-Lite (/29). |
| 192.0.2.0/24 | 192.0.2.0–192.0.2.255 | 256 | Documentation | Assigned as TEST-NET-1, documentation and examples. |
| 192.88.99.0/24 | 192.88.99.0–192.88.99.255 | 256 | Internet | Reserved. Formerly used for IPv6 to IPv4 relay (included IPv6 address block 2002::/16). |
| 192.168.0.0/16 | 192.168.0.0–192.168.255.255 | 65,536 | Private network | Used for local communications within a private network. |
| 198.18.0.0/15 | 198.18.0.0–198.19.255.255 | 131,072 | Reserved network | Used for benchmark testing of inter-network communications between two separate subnets. |
| 198.51.100.0/24 | 198.51.100.0–198.51.100.255 | 256 | Documentation | Assigned as TEST-NET-2, documentation and examples. |
| 203.0.113.0/24 | 203.0.113.0–203.0.113.255 | 256 | Documentation | Assigned as TEST-NET-3, documentation and examples. |
| 224.0.0.0/4 | 224.0.0.0–239.255.255.255 | 268,435,456 | Internet | In use for IP multicast. |
| 233.252.0.0/24 | 233.252.0.0-233.252.0.255 | 256 | Documentation | Assigned as MCAST-TEST-NET, documentation and examples. |
| 240.0.0.0/4 | 240.0.0.0–255.255.255.254 | 268,435,455 | Internet | Reserved for future use. |
| 255.255.255.255/32 | 255.255.255.255 | 1 | Subnet | Reserved for the local broadcast destination address. |
Private IPv4 networks
Public routers don’t route private network addresses on the public internet. Private hosts require Network Address Translation (NAT) at a router to communicate directly with public networks. NAT acts like a two-way mirror that allows private networks to connect to the public internet while staying invisible from the public internet.
Similarly, a Virtual Private Network (VPN) bridges two private networks across the public network by creating a secure tunnel and encrypting traffic that crosses the tunnel.
The following three address ranges are reserved for private networks:
10.0.0.0/8172.16.0.0/12192.168.0.0/16
IPv4 packet structure
An IPv4 packet consists of a header and data (a payload). A packet is like a physical package or envelope with the source and destination addresses written on it. Some packet fields even resemble the types of delivery seen on physical mail, e.g., first class, standard, priority.
Figure 2: IPv4 packet structure with fields and field sizes in bits.
The IPv4 packet header consists of 14 fields:
Version: The 4-bit version of the IP protocol that is used in the packet header. For IPv4, it is equal to 4.
Internet Header Length (IHL): The 4-bit length of the header that specifies the number of 32-bit words in the header. The header size depends on the optional 14th field (Options). The minimum value is 5 (160 bits or 20 bytes), while the maximum value is 15 (480 bits or 60 bytes). If the IHL field is greater than 5, the Options field is present and must be considered.
Type of Service (ToS) or Differentiated Services (DS): Is comprised of two fields that help routers prioritize traffic flow:
Differentiated Services Code Point (DSCP): A 6-bit service number used to differentiate various services, such as data streaming and Voice over IP that run over the Internet Protocol.
Explicit Congestion Notification (ECN): A 2-bit value used for optional end-to-end notification of network congestion without dropping packets. Both endpoints of the network must support ECN to use it.
Total Length: A 16-bit packet length in bytes, including both the header and the payload. The minimum size is 20 bytes for a packet with only a header, and the maximum is 65,535 bytes.
Identification: A 16-bit unique identifier for related fragments of a single IP packet.
Flags: A 3-bit value used to control and identify fragments:
- bit 0: Reserved. Always set to zero.
- bit 1: Do not Fragment (DF). When the DF flag is set and fragmentation is required to route the packet, the packet is instead dropped.
- bit 2: More Fragments (MF). The MF flag is set for all fragmented packets except the last fragment of the packet.
Fragment offset: A 13-bit value that specifies the offset, in bytes, of a particular fragment relative to the beginning of the original unfragmented IP packet. The offset for the first fragment is always 0, and other offsets are multiples of 8 since fragments are specified in units of 8 bytes. The maximum offset is 65,528 bytes.
Time to live (TTL): An 8-bit value of the maximum hop count of the packet. Each time the packet reaches a router, the value is decreased by one. If the TTL hits 0, then the router discards the packet. This ensures that packets don’t endlessly route through networks and cause network congestion.
Protocol: An 8-bit value that defines the protocol used in the payload of the packets.
Header checksum: The 16-bit IPv4 header checksum that is used to check for errors in the header. When a packet arrives at a router, the router calculates the checksum and compares it to the checksum in the header. If the values don’t match, the packet is discarded. Higher-layer protocols check the payload if necessary. When a packet arrives at a router, it decreases the TTL in the header, which requires the header to calculate a new checksum.
Source address: A 32-bit field that identifies the IPv4 address of the packet’s sender.
Destination address: A 32-bit field that identifies the IPv4 address of the packet’s receiver.
Options: This field is rarely used. Common uses are to record the route a packet takes to the destination or to request a specific route to a destination. Also, an IP header must be a multiple of 32 bits. If the Options field is used and the header is not a multiple of 32 bits, the rest of the Options field is padded with 0 bits to create a multiple of 32 bits.
IPv4 fragmentation
The design of IPv4 accommodates networks of diverse quality, varying transmission speed, and varying Maximum Transmission Unit (MTU). Routers fragment packets when sending them to a network with a smaller MTU. The maximum size of each fragment sent in a single network-layer transaction is the outgoing MTU minus the IP header size. Hosts reassemble the fragmented packets.
When a router receives a new packet, it examines the destination address and determines the outgoing interface to use and that interface's MTU. When the MTU is smaller than the packet size and “Do not Fragment” is set to 0, the router fragments the packet.
Each new packet has the following changes:
- The Total Length field gets the fragment size.
- The More Fragments (MF) flag is set to 1 for all fragments except the last one, which is set to 0.
- The Fragment Offset field is set to the offset of the fragment from the start of the original data payload, measured in units of 8-byte blocks. For example, for an MTU of 1,600 bytes and a header size of 20 bytes, the fragment offsets are multiples of (1,620 - 20) / 8 = 200, as follows: 0, 200, 400, 600, and so on.
- The Header Checksum field is recomputed.
The receiver knows that a packet is a fragment if one of the following conditions is true:
- The More Fragments flag is set to 1. This is true for all fragments except the last.
- The Fragment Offset field is nonzero. This is true for all fragments except the first.
The receiver identifies matching fragments using the source and destination addresses, the protocol identifier, and the identification field and reassembles fragments according to their fragment offset values.
What is the limitation of the ipv4 protocol?
IPv4 address space exhaustion
IPv4 uses 32-bit addresses. This limits the address space to 2^32, or roughly 4.3 billion addresses. It doesn’t take a mathematician to realize that if all of the 8 billion people in the world had a computer to connect to the internet, IPv4 would not meet the demand for addresses.
The rapid growth of internet users and computing devices that use IP data services depleted the pool of available IPv4 addresses faster than anticipated. To slow the exhaustion of the available address space, several solutions were implemented:
- Classless Inter-Domain Routing (CIDR): Instead of using the initial fixed-length network groups of Class A (a network prefix of 8 bits), Class B (a network prefix of 16 bits), or Class C (a network prefix of 24 bits), variable-length prefixes, also known as Variable-Length Subnet Masking (VLSM), were used.
- Unnumbered interfaces: A point-to-point link (also called a transit link) that does not have an IP network or subnetwork number but still has an IP address. Transit links route packets and reduce IP address use, management, and configuration.
- NAT: A method of mapping one IP address space into another by modifying network addresses in IP headers while they transit a router.
Despite these measures, the IPv4 address pool of the internet began to exhaust in early 2011.
The long-term solution to address exhaustion is a new version of the Internet Protocol, version 6 (IPv6). It provides a vastly increased address space, improved route aggregation to simplify routing tables, and offers large subnetwork allocations to end users. It has been formally in use since 2006. However, IPv4 and IPv6 are not directly interoperable, so they need to use NAT or a tunnel for a packet in one IP version to traverse the other.
IPv4 security issues
Major security concerns with IPv4 include address hijacking, address spoofing, and Distributed Denial-of-Service (DDoS) attacks.
IPv4 address hijacking depends on the Border Gateway Protocol (BGP) to route traffic to fake networks that then maliciously respond to requests sent to those IP addresses. Often, the attacker’s goal is to disrupt normal network operations. Intentional tampering of BGP routes is also a common way that governments choose to remove their citizens’ access to certain internet applications or websites.
DDoS attacks flood a target server with fake traffic until the server cannot serve legitimate users. It’s like you want to buy coffee from your local coffee shop, but thousands of robots in trench coats suddenly jump in line ahead of you.
Often, multiple types of attacks are combined toward the same goal. For instance, DDoS attacks can use address spoofing to not only flood the target but also prevent easy fixes like blocking the attacking source IPs.
