Understanding Bad Bots and How to Prevent Botnet Attacks
Imagine leaving your front door unlocked in a busy city. At first, everything seems fine, but without warning, strangers start slipping in—some just wandering or snooping, others stealing valuables. This is how the internet works when left unprotected.
Similarly, in the digital world, every connected device is a potential entry point, and cybercriminals use automated scripts, known as bots, to probe, exploit, and take control of vulnerable systems. In fact, the internet is teeming with bots. But in general, bots can perform various tasks, ranging from helpful automation to malicious activities.
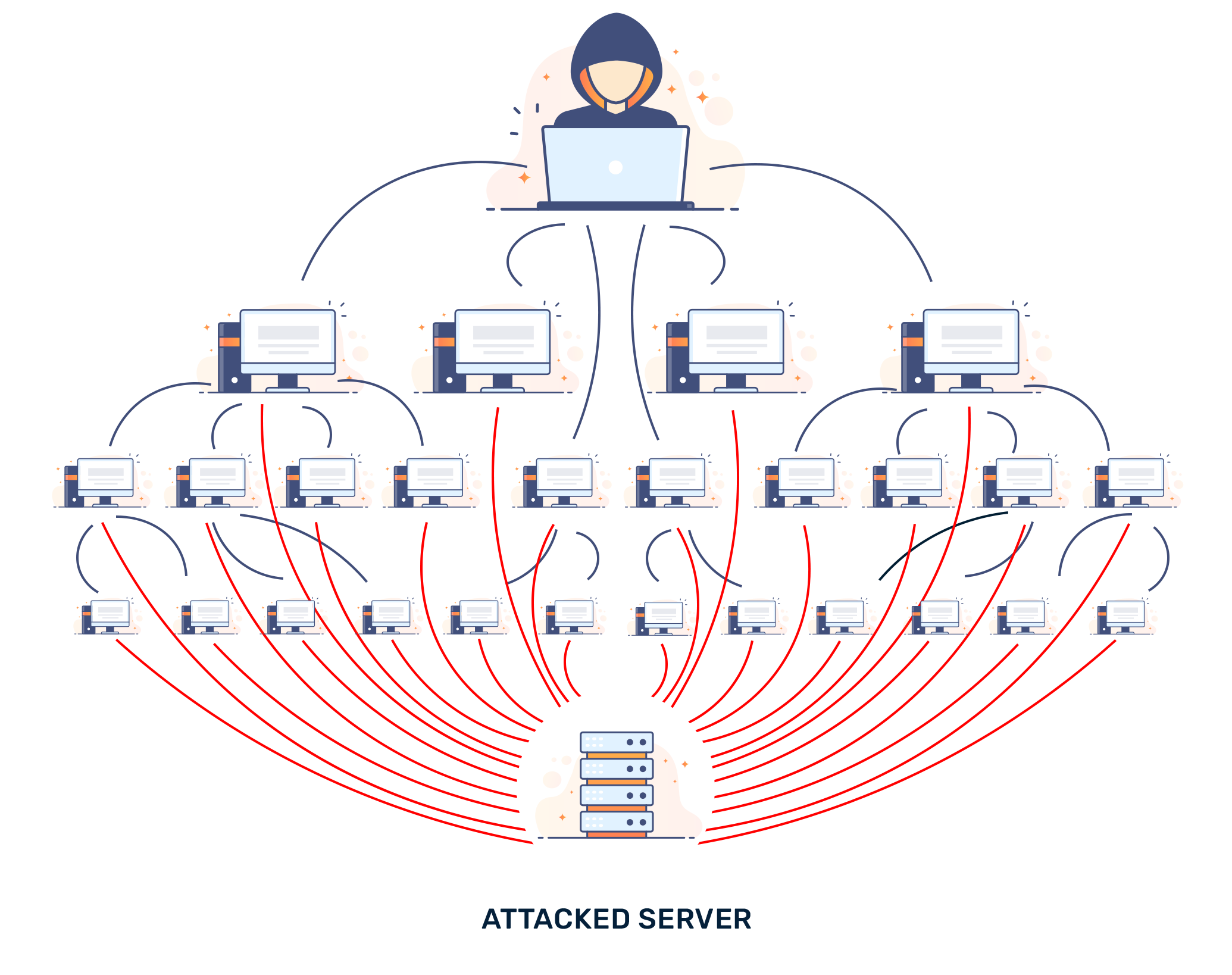
When multiple bots are coordinated under a single control, they form a "botnet." These botnets can be used for distributed denial-of-service (DDoS) attacks, credential stuffing, data scraping, and various other cyber threats. Understanding how bots function and how botnets operate is crucial in defending against modern cyber threats.
In this article, we will explore bot mechanics, real-world examples, and the strategies used to mitigate bot-related security risks.
Understanding bots
A bot is an automated script or software application that performs repetitive tasks over the internet. Some bots serve beneficial purposes, such as search engine crawlers that index web pages, uptime monitoring services that check website availability, chatbots that provide customer support, and automated assistants like Siri, Alexa, and Google Assistant. However, not all bots are helpful. Some are created for malicious purposes, including:
- Web scrapers that extract content from websites without permission.
- Credential stuffing bots that try stolen username-password pairs on multiple sites.
- Spam bots that post promotional content on forums and social media.
- DDoS bots that overload websites with excessive traffic.
For example, a simple bot can be written in Python using the requests and BeautifulSoup libraries to scrape content from a website:
import requests
from bs4 import BeautifulSoup
url = "https://example.com"
headers = {"User-Agent": "Mozilla/5.0"}
response = requests.get(url, headers=headers)
soup = BeautifulSoup(response.text, 'html.parser')
# Extract all links from the page
links = [a['href'] for a in soup.find_all('a', href=True)]
print(links)
While this example is harmless, unethical actors often use similar bots to scrape copyrighted content, prices, or personal data.
What are bad bots and botnets?
A botnet, short for "robot network," is a collection of compromised devices, often referred to as "zombies," that are controlled by an attacker. These devices can range from personal computers to IoT devices like security cameras and smart fridges.
Botnets typically follow one of two architectures. The first is a centralized model, where a single command-and-control (C2) server sends instructions to infected devices. This model is easier to manage but is vulnerable to takedown by authorities. The second model is decentralized, operating as a peer-to-peer network in which infected devices communicate with each other. This structure makes it more difficult to dismantle since there is no single point of failure.
How botnets are built and operated
Botnets are built through a process that begins with infection. Attackers use malware, phishing schemes, or software exploits to compromise devices and gain control over them. Once infected, these devices establish communication with the attacker, often via HTTP, IRC, or peer-to-peer protocols. After that, the botnet carries out its designated tasks, which may include sending spam emails, conducting DDoS attacks, or stealing credentials.
Example: A simple bot command script
The following is an example of a bot client that connects to a command-and-control server:
import socket
server_ip = "192.168.1.100"
port = 8080
# Connect to C2 Server
bot_socket = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
bot_socket.connect((server_ip, port))
while True:
command = bot_socket.recv(1024).decode()
if command == "attack":
print("Launching attack...") # In reality, this would execute malicious actions.
elif command == "stop":
print("Stopping bot activity.")
break
While simple, real botnets use more advanced techniques to evade detection and persist on infected devices.
Types of attacks botnets launch
Botnets are used to carry out a wide range of cyberattacks, each with varying degrees of sophistication and impact. A common attack is the DDoS, where a botnet floods a target server with excessive requests, overwhelming its capacity and rendering it inaccessible. These attacks can disrupt businesses, websites, and even critical infrastructure.
Credential stuffing is another prevalent attack, in which bots use stolen username-password pairs to gain unauthorized access to user accounts. This is particularly dangerous when users reuse passwords across multiple services.
Botnets are also frequently employed for web scraping, where automated bots extract content, pricing data, or proprietary information from websites without permission. Some bots are even designed for ad fraud, generating fake impressions and clicks to deceive advertisers and drain marketing budgets.
Another common bot-driven attack is spam distribution, where infected devices send large volumes of unsolicited messages to spread malware, phishing links, or promotional scams. More advanced botnets engage in data exfiltration, silently infiltrating systems to steal sensitive information, such as financial data, intellectual property, or personal records.
In addition to these threats, botnets facilitate malware distribution by automatically spreading malicious software to unprotected systems. Many modern malware strains rely on botnets to propagate ransomware, trojans, and worms. These attacks can have devastating consequences, from financial losses to reputational damage.
Real-world botnets and their impact
Botnets have caused significant damage in the real world. The Mirai botnet, which emerged in 2016, infected IoT devices such as cameras and routers, launching record-breaking DDoS attacks that took down major websites, including Dyn, Twitter, and GitHub.
Another notable botnet is Emotet, which initially functioned as a banking trojan before evolving into a modular malware delivery system. It has been used for spam campaigns, ransomware distribution, and credential theft. The 3ve (Eve) botnet, on the other hand, was a large-scale ad fraud network that generated fake ad clicks before it was dismantled by Google and law enforcement in 2018.
How to Prevent Botnet Attacks
Individuals and organizations can take several measures to defend against botnet threats. Keeping software updated is crucial in preventing attackers from exploiting known vulnerabilities. Using strong, unique passwords reduces the risk of credential stuffing attacks, while exercising caution with emails helps avoid phishing scams. For IoT devices, disabling unnecessary services and changing default credentials can reduce the attack surface.
Businesses and website owners can implement more advanced defense:
- Rate limiting helps control automated login attempts.
- CAPTCHAs and challenge-response systems discourage bot-driven activity.
- Deploying a web application firewall (WAF) is another effective measure to block malicious requests.
- Monitoring traffic for anomalies can help detect unusual spikes that may indicate a bot attack.
Example: Blocking Bots with a web application firewall (Nginx example)
You can configure an Nginx WAF to block requests from suspicious user agents:
server {
listen 80;
server_name example.com;
if ($http_user_agent ~* "bot|crawler|spider") {
return 403;
}
}
Conclusion
Bots and botnets play a significant role in modern cybersecurity, with some being helpful and others causing widespread damage. Understanding how these systems work enables individuals and businesses to better defend against malicious bots.
By implementing best practices such as firewalls, rate limiting, CAPTCHAs, and anomaly detection, organizations can mitigate botnet threats and protect their digital assets from exploitation.
