What is a Man In The Middle (MITM) Attack?
Introduction
Man-in-the-middle usually refers to a type of cyber attack. It's a broad term that describes any device between your computer and the destination.
When an attacker positions themselves between your data and its destination, you can imagine the risk to personal information, passwords and credentials, financial information, browsing history, and more. A man in the middle could steal all of this sensitive information.
Imagine you called your friend Jane. You tell Jane all about your day and recent doctor's appointment and nothing seems amiss. Unfortunately, your seemingly secure call has been monitored this entire time. Jim, your worst neighbor, tapped the wired connection and now knows everything about your day and some sensitive medical information. A man-in-the-middle attack literally occurs when someone places themselves in the middle of two connected devices.
How an MITM attack happens
MITM attacks tend to happen when you use an unsecured network or run outdated software. It begins with inspection. When an attacker monitors outgoing traffic to determine their next course of action. They might check for insecure traffic, steal cookies, or inject packets into the data stream.
Eventually, the attacker finds a way to slot themselves in the middle. They might use a stolen SSL certificate or exploit vulnerabilities in older SSL versions. Their goal is to enter the connection as an invisible entity between you and a destination server.
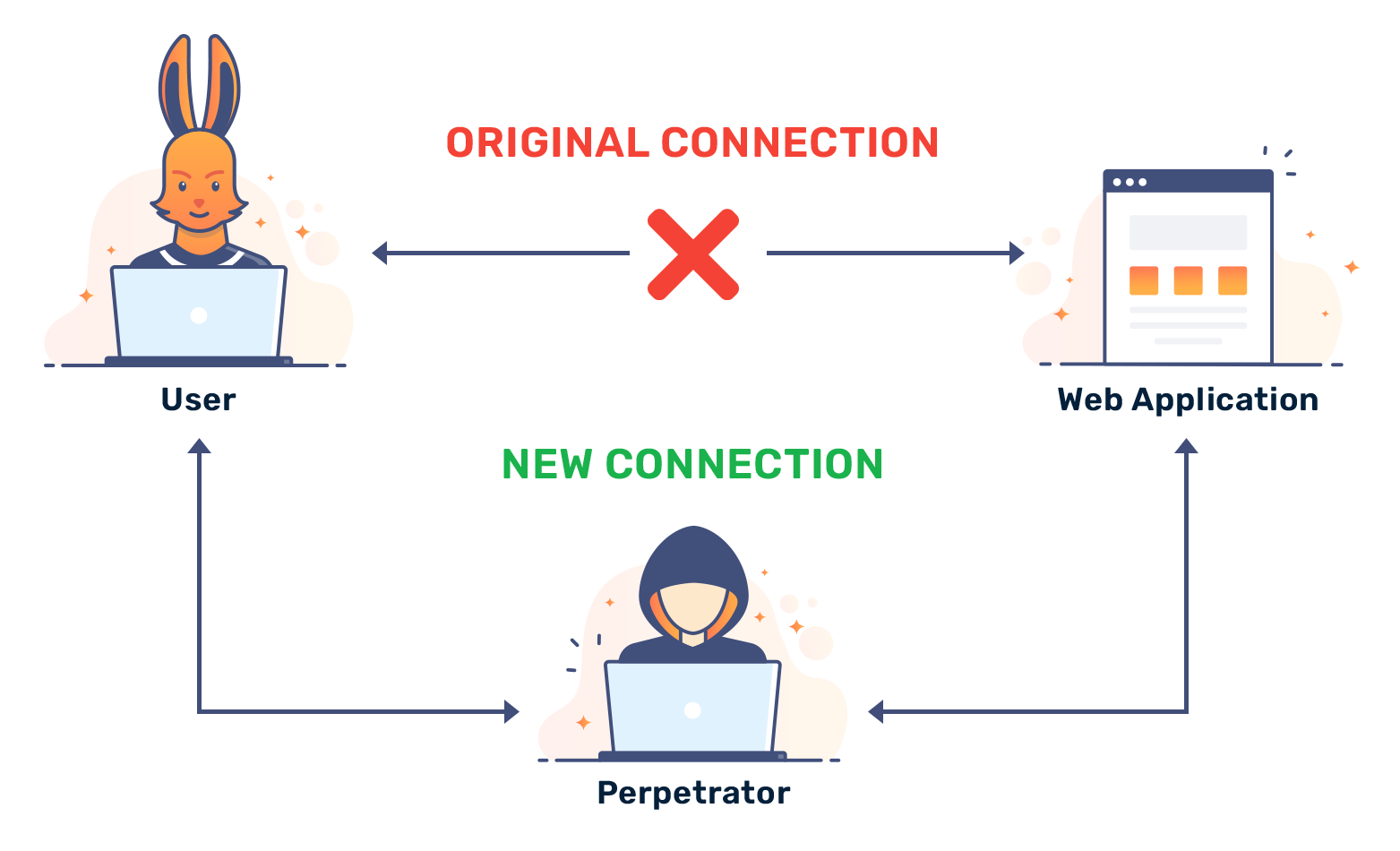
Once the MITM attack is created, the attacker has complete control over the data they intercept. They can modify data on-the-fly to fool a destination server into transferring money to them and steal personal information like SSN numbers, your date-of-birth, and more.
Preventing MITM attacks
When executed well, MITM attacks can cause financial loss and damage to a victim’s identity. Whether the MITM attack is targeted or not, attacks often require the exploitation of a vulnerability in old software or physical presence to intercept traffic.
MITM attacks can be mitigated using a secure tunnel and up-to-date software, but no solution is foolproof. Here are some practices that can be taken to reduce your chances of being caught by an attacker:
- Refrain from using public networks
- Keep your OS updated
- Use source verification and strong encryption
