How does a Web Application Firewall and WAF rules work?
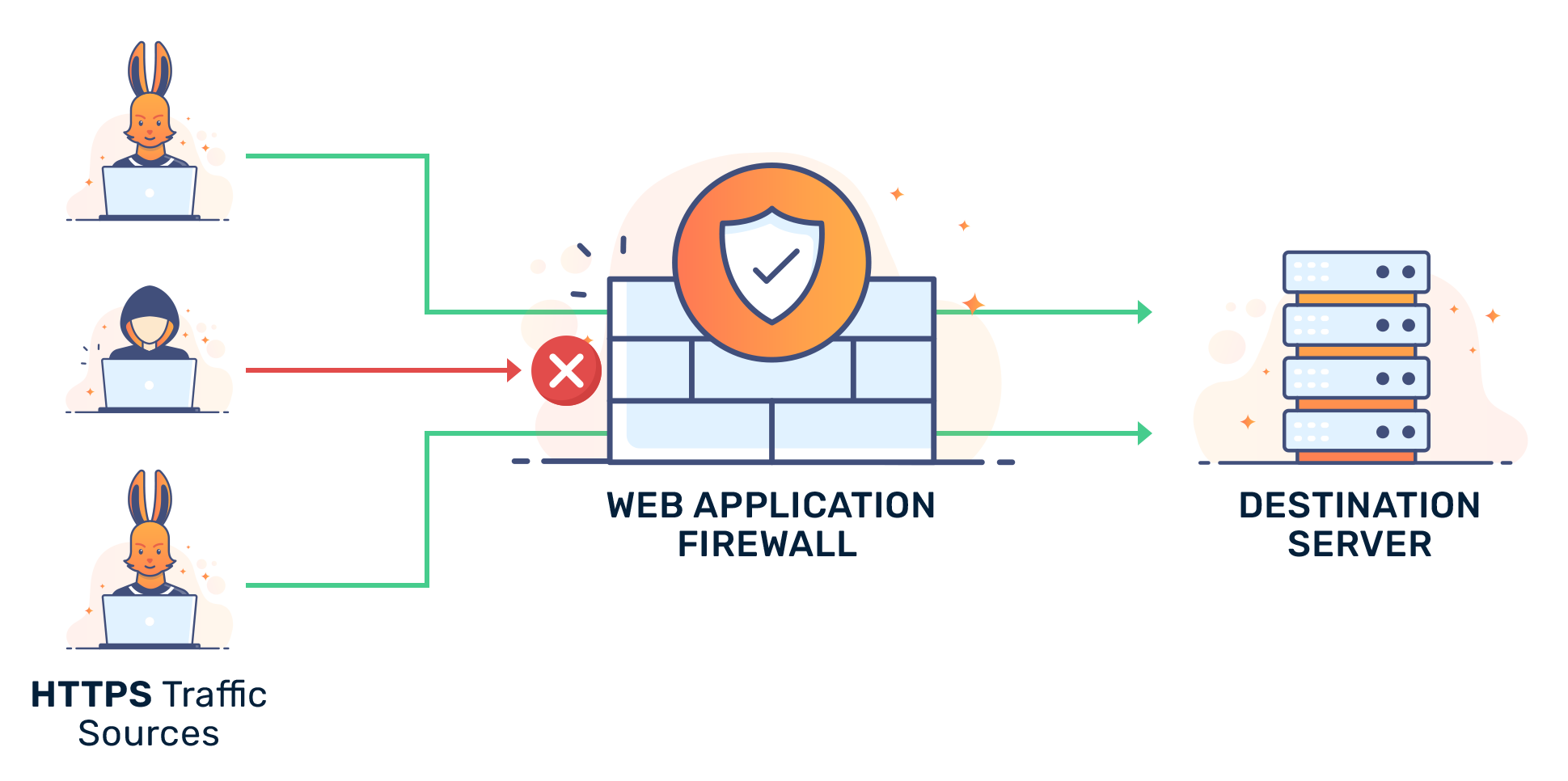
A Web Application Firewall (WAF) is a middleman that sits between web applications on a web server and the Internet. A WAF serves two major functions: preventing malicious traffic from reaching web applications hosted on a server and preventing unauthorized data from leaving the web server.
In the Open Systems Interconnection (OSI) seven-layer model, a WAF operates at the application level, which is the seventh and highest level. In particular, it filters Hypertext Transfer Protocol (HTTP) traffic to prevent common web attacks that exploit a web application's known vulnerabilities. Common attacks include:
- structured query language (SQL) injection
- cross-site scripting (XSS)
- cross-site forgery
- file inclusion
- cookie poisoning
- broken authentication
- sensitive data exposure
- XML external entities (XXE)
- broken access control
- security misconfigurations
- insecure deserialization
The early versions of WAF came to market in the late 1990s when the first types of web attacks became more prevalent. Early WAFs were commercial products which limited their use. However, in 2002 an open source project ModSecurity was started to make WAF more accessible.
The core WAF rules for protecting web applications are based on OASIS Web Application Security Technical Committee’s (WAS TC) analysis of web attacks and application vulnerabilities. In 2003 the rules set was expanded and standardized through the Open Web Application Security Project (OWASP) database of web security vulnerabilities.
How Web Application Firewalls and rules work
To prevent attacks, a WAF monitors and examines every single data packet of HTTP traffic going in and out of a web server to ensure that the data packets are safe. WAFs are not designed to defend against all types of attacks. They are used in conjunction with other network security solutions such as network firewalls and intrusion prevention and detection systems.
They use a combination of managed rules or policies and rule-based logic, data parsing, and signatures to detect and prevent the attacks. They depend on the quality and quantity of provided rules and signatures. The attacker may use browser emulation, obfuscation, virtualization, and IP obfuscation to attempt to bypass WAFs.
Policies establish what malicious traffic and safe traffic look like. Broadly, these policies fall into two categories: block lists (negative security model) that protects against known threats or allow lists (positive security model) that only admits pre-approved traffic. Both approaches have their advantages and disadvantages, which is why many WAFs employ both in a hybrid security model.
Conceptually, a WAF works like a reverse proxy. A proxy typically protects client machines’ identities from web servers by positioning itself in the middle of the data flows between client and server machines. For a WAF, its protection acts in the reverse direction. It positions itself in the middle of data flows between the server and client machines to protect the server from potentially malicious traffic originating from clients.
WAFs can be deployed as a transparent bridge, transparent reverse proxy, or reverse proxy. Transparency refers to the fact that HTTP traffic is sent directly to the web application. Therefore, the WAF works transparently between the client and server without either noticing. On the other hand, when a reverse proxy is used, the HTTP traffic is sent to the WAF directly, which then sends the filtered traffic to web applications. These have the benefit of obfuscating the web applications behind the WAF. However, they may introduce performance latency.
Ways to deploy a WAF
A WAF can be implemented in software or hardware, running in an appliance device, or a typical server running a common operating system. There are three major ways to deploy a WAF on a web server: network-based, host-based or cloud-based.
- Networked-based WAF: In a network-based WAF, hardware or physical equipment is used to sit in between server and client traffic. The main advantage of network-based WAFs is that they minimize latency because the protection operates through a separate physical device on-site. However, network-based WAFs are usually the most expensive option.
- Host-based WAF: For a host-based WAF, protection comes from software installed on the web server itself. Like networked-based WAFs, host-based WAFs are on-site and minimize latency. However, host-based WAFs consume the resources of the web server because they don't reside on a separate physical device, unlike network-based WAFs. Host-based WAFs may also be costly because they require a web server to be optimized so that deployment of a host-based WAF doesn't degrade performance.
- Cloud-based WAF: The main advantages of cloud-based WAFs are affordability and simplicity. Cloud-based WAFs are typically offered as a service for a monthly fee and do not require hefty upfront investment such as buying physical equipment, like network-based WAFs. Cloud-based WAFs are also very easy to implement. Often, a DNS change to redirect traffic to the cloud-based WAF service is all that is necessary. The main downside of cloud-based WAFs is that the protection is not on-premise and the protection is offered by a third-party. Providers lack full knowledge of the policies and strategies employed by cloud-based WAFs.
